| ||||
|
You may redistribute this newsletter for non-commercial purposes. For commercial use contact jack@ganssle.com. To subscribe or unsubscribe go here or drop Jack an email. |
||||
| Contents | ||||
| Editor's Notes | ||||
|
Tip for sending me email: My email filters are super aggressive and I no longer look at the spam mailbox. If you include the phrase "embedded" in the subject line your email will wend its weighty way to me. I'm not sure if April 1 is regarded as April Fool's Day in the entire world, but here in the West it's a day for pranks and jokes. You may want to keep that in mind while reading this issue of the Muse. |
||||
| Quotes and Thoughts | ||||
|
“In theory there is no difference between theory and practice. In practice there is.” - Yogi Berra |
||||
| Tools and Tips | ||||
|
Please submit clever ideas or thoughts about tools, techniques and resources you love or hate. Here are the tool reviews submitted in the past.
|
||||
| The Vote | ||||
|
News Analysis President-elect Bubba "the can man" Jones expressed surprise at his unexpected win in last night's quadrennial elections. With 100% of the precincts reporting in, Jones overwhelmed the incumbent by acquiring an astonishing 65.536% of the vote. His opponent garnered just 1.024%, with the rest strangely going to an as-yet unidentified candidate named "hckergrrl". Seeming confused by the crush of reporters and well-wishers Mr. Jones continued to hover protectively over his shopping cart. Suspiciously eying members of his new Secret Service detail he was heard complaining about attempts to take his collection of aluminum cans and old clothes. "Nobody gonna rip off my stuff," he muttered. "Dem cans worth 2, mebbee 3 bucks." Hustled into the waiting limo he expressed delight at the prospect of sampling the car's mini-bar. Tonight the president-elect remains in seclusion in the Blair House, hastily-recruited aides telling reporters he was "sleeping off the effects of a trying campaign." Though it remains unclear just how Mr. Jones won the presidential election despite his not having been on the ballot, and why the incumbent's Democratic opponent gathered not a single vote, this reporter has seldom seen an election run in such an efficient and forthright manner. Contrast last night's speedy decision with the rancorous climate of 2000, where slim margins and problems with paper ballots led to a court's decision that disenfranchised voters nationwide. Modern technology has eliminated the age of hand-counted ballots. "Hanging chad" will be nothing more than a colorful phrase recalled in history books. Recounts now take seconds. Never again will the courts decide an election. Call 2024 "The Year of the Electronic Vote." Thank the citizens of Florida for our electronic elections. Misplaced ballots, poorly-punched selections, and perhaps even outright corruption held the 2000 presidential race in suspense for weeks. Determined to avoid the scandals, the Sunshine State replaced thousands of antiquated manual machines with the latest of electronic vote counters. High tech touch screens instantly record each voter's decision, transmitting the results to a national database when the polls close. Recounts involve nothing more than a retransmission of the data, since we know the computers themselves are deterministic, immune from fraud, and cannot make mistakes. The CriticsLuddites suggest that we rely too much on software for critical systems, sometimes referring to the Navy's unfortunate Smart Ship program. Recall, though, that after the sixth fleet attacked Palau in Micronesia earlier this year, the review board showed the logic of that autonomous decision: the computer realized that Palau lacked the ability to shoot back. "This clearly shows the efficacy of a system designed to win wars," Admiral Turgidson noted, "the system created a war that it could not lose. The subsequent divide overflow that crashed the flagship's propulsion system was entirely unanticipated." (Reports indicating the ship was overwhelmed by an unruly band of Caroline Islanders who turned it into a floating casino bar remain unconfirmed). Others mentioned last month's recall of 600,000 Internet-ready automobiles when hackers found they could deflate the cars' tires, reprogram the engine controllers to emit constant backfires, and lock the windows up and doors closed with the heat on "high". Detroit reluctantly admitted to a buffer overflow problem but stated these were minor problems blown out of proportion by the press. Spokesman Graeme Kirchner once again urged passage of the National Anti-Hacking Act, saying "these bloody unsupervised latch-key kids run rampant through the computer networks. Parents should keep them bloody well away from the bloody home computer." To get to the truth of software risks I interviewed Tom Thorten, lead software engineer of the SmartVote system employed so successfully in this week's elections. Me: "Mr. Thorton, isn't this device what you folks call a safety-critical system?" TT: "Nah, this isn't a safety-critical app. That's for avionics and nuke plants. No one's gonna die if this thing crashes. Hey, if there's a problem with this box ya just reset and carry on. Pretty much like any chunk a code." Me: "How can you ensure the vote is tabulated correctly?" TT: "Vote? Is that what this thing does? They just told me what to put on the LCD and how to log the data. The spec was pretty light, know what I mean?" Me: "No." TT: "Well, it's like any system. The boss is wrapped up with making promises to customers. Her boss is usually off testifying somewhere, and the Big Boss is still awaiting extradition from Barbados. It's pretty much up to me what this puppy does." Me: "How was this tested?" TT: "Oh, the usual, ya know? We pounded on it some, then Bob's kid (ya know the one? Cute little tyke?) played with it for a while. It was hell getting the ice cream outa the PCB. Then we stuck it down in Florida. Yeah, a few kinks. We figured most of those old folks wouldn't hit the screen too fast, but when they did, man that ole priority inversion thing hit bad, know what I mean?" Me: "No. What happens to the data?" TT: "Oh, we toss it into one of those embedded DBs, a cool relational thing. Sure wish it was reentrant; those corruption problems are killing us. Then at the end of the day we TCP it to Republican National Headquarters. Or was it the Dems? One of them, they keep changing the IP address on us. Little do they know - we stuck in a back door that lets us set a new IP at will. Saves a recompile every time they change their freakin' minds. Those dudes then dump it all into the National Database. But our box logs the data and ships it out. After that it's not my problem." Me: "So if these things are on the net, what about security?" TT: "Well, I guess some folks might want to hack their way in, but it's pretty unlikely. We're running Embedded Win eXtraP, the most secure Win OS ever. It's so good it keeps downloading patches and fixes; hey, the system we ship evolves to something else over the course of a year. It's like, organic, man. No one really even knows what the code base looks like now. Pretty awesome, know what I mean?" Me: "So no one can break in?" TT: "Nah, probably not. Well, not at least if the users had a brain. I can't figure out why our customers never seem to set up a password like the read.me tells them to. Half them systems are wide-open! You know users, though. It's like my cable modem, you know? I see all sorts of open systems on the cable. My kid even ripped off some lawyer's Amex numbers from a Word doc on this dude's exposed C drive. Sure am proud of that little rug rat." Me: "In Florida some people struggled with system lockups. What happens then?" TT: "Oh, jeez, customers complain about every little thing. Just reset it, for Pete's sake, and don't get your panties in a wad." Me: "But what happens to all of that data?" TT: "Bit bucket, I guess." Me: "Huh?" TT: "/dev/null. You know." Well, the arcane language of the computer professional was something we English majors didn't learn in Princeton's class of 1958. But I feel it's only proper to delegate the complexities of encryption, computers, and corporate accounting to those professionals who know these things best. Proper government oversight, as mandated in the Public Security and Trusted Computing Act, insures the nation's interest will be met. Mr. Thorten assured me that the Transportation Security Administration will start examining his code base "real soon now". One Person, One VotePresident-elect Jones inherits a fractious constituency, divided in part by the nature of the very vote that gave him the nation's highest office. Perhaps the largest issue brought to the fore by various commentators in this post-election day is that of universal suffrage. Just what does "one person one vote" mean in a high tech age? Does your vote matter? The 2000 presidential contest resulted in a razor-thin margin. Some contend that it makes no difference who had won that election, since the difference in votes was in the noise. Either candidate would have had the support of half of the electorate. The narrow margins raised questions only recently resolved by the Supreme Court. In a unique move the nine Justices deferred to the analysis of statisticians, who argued that uncertainty is part and parcel of every data gathering exercise. They pointed to the Gallop Polls which have long had an associated error band. In Florida and other states an automatic recount is mandated when a contest results in only 0.5% difference or less between the candidates. The statisticians argued that such a small delta is meaningless, that no amount of recounting or runoff elections would express the will of the people with any more certainty. Justices bought this argument, resulting in the famous 3 sigma election rule: if the error does not exceed 3 sigma, why worry? As the Chief Justice wrote in his majority opinion, "hey, this is the government. You just can't expect nine 9s." After that landmark decision the liberal press was taken to task for promulgating the idea that voting was a quaint but pointless exercise. One wag suggested, for instance, that a Republican in Maryland (there are a few) shouldn't bother casting a vote in state-wide elections. The long and overwhelming history of Democratic successes there suggests that Democrats waste their time if they vote, and Republicans waste their spirit. To a first approximation the outcome seems preordained. The old saw "my vote negates yours" now reads "my vote counts as little as yours." This reporter would argue that every vote counts, just as it did when the Founding Fathers brought forth this great nation more than 200 years ago. The Supreme Court's unfortunate decision did not factor in the power of technology to solve most ills. I see no reason why our scientists can't employ the same technology that so accurately guided the Mars Climate Observer to the surface of Mars, or that enabled Armstrong's triumphant Apollo 13 landing, to ensure every vote counts. Don't be misled by critics who contend that, in the absence of paper records, an e-recount is nothing more than another database download. Does a ballot whose chad-clinginess is interpreted by an army of well-intentioned but exhausted observers better represent the will of the people? The new technology of electronic voting insures every person is properly represented. Your touch-screen selection instantly tips the balance in favor of your candidate. The margin for error, due to the supreme number-crunching power of the computer, is surely zero. I look forward to the day I can vote from home using the power of the Internet and the security inherent in the most popular operating systems. This is Daniel Shorrt. Thank you. |
||||
| Embedded Definitions | ||||
|
Things change quickly in this industry; new words and expressions appear seemingly every day, while the meaning of older terms evolve. So here's an update. Ada - The programming language that promised to deliver very high-quality code at a reasonable price. In practice it was found to fulfill those promises, though at the cost of annoying programmers by making them stick to a very strict syntax. So it was all but abandoned in favor of inferior alternatives. After all, debugging is sort of fun! Agile method - A reaction to Big Up-Front Design, the agilists purport that nothing is known, nor will anything be known until customer acceptance, and therefore you better start coding, right now. Algorithm - A problem's solution, invented by Al Gore. Assembly language - The only computer language that allows unlimited artistic expression, assembly was invented by FDR during the Depression as a jobs program. Big Up-Front Design - The traditional approach to building programs. It relies on the proven assumptions that the customer really knows what he wants, has expressed those ideas clearly and completely in the specification document, and that the future never brings change. Bit banging - An abusive programming technique that has sent millions of bits into therapy. Bugging - The part of programming that includes specification, design and coding, but that ends before any sort of testing starts. Primarily involves seeding defects into the code. See Debugging. C - A programming language whose syntax is so loose most C compilers will happily accept the telephone directory as syntactically-correct. C++ - An object oriented programming language which has an on-going committee whose goal is to add so many obfuscating features that no single individual really understands all of its nuances. COBOL - The only programming language which will still be around in the year 10,000 AD. See 8051. Clever code - "Debugging is twice as hard as writing the code in the first place. Therefore, if you write the code as cleverly as possible, you are, by definition, not smart enough to debug it." (Brian W. Kernighan) Cost Plus Contract - The opportunity to never say "no" to a feature request, never deliver, and keep vast numbers of people on the payroll till someone in Congress (in some other Congressional district) notices. Debugging - Removing the defects so laboriously inserted during bugging. Embedded System - Who knows? Once an embedded system was something using an 8051. Now they include PowerPCs and Pentiums, plus desktop OSes like Linux and Windows. Maybe an embedded system is anything with a computer in it that's not a PC or Mac. Except those usually have many processors embedded inside. Engineer - A person trained to solve problems. If there are no problems, an engineer will create a few. Estimation - The act of putting together a schedule which, if developer productivity triples and electrons can be moved faster than the speed of light, will result in funding of the project. See Clairvoyance. Firmware - A product marketed by Pfizer that comes in little blue pills. Firmware standard - The platinum rod maintained in a temperature-regulated environment by the National Institute of Standards and Technology to measure ED. Flash memory - A technology invented so no program needs to be completed. Ship with a boot loader and eternally email updates till the customer is so frustrated he gives up, long after his check has cleared. Forth - An older language whose adherents once sent me 20,000 emails when I poked some fun at it, ah, so, uh, Forth is the world's most popular computer language and is perfect for a wide range of applications, including all of them. Free() - obsolete; unused. See malloc(). Glitch - an anomaly in your program. In anyone else's program it's called a "bug." Hacking - The art of software development as taught in many universities. Hard core - A microprocessor embedded in fixed cells on a programmable device like an FPGA. What - did you expect some other definition? Hard Real-time - A sentence resulting from a felony. Int - A data type that holds some number of bits which varies depending on the processor, compiler and wind direction. Kernel - An important ingredient of Taco Bell's products, consumed by developers around the world. Linux - The golden child of operating systems. Answer to life, the universe, and everything. Most excellent example of perfection. Utterly without fault. Maintained by a band of devoted faithful whose primary mission is to strike down all favorable references to *that* other operating system which was spawned by the devil, sold by his evil minions, and used only by clueless GUI-loving newbies. Under no circumstances see Windows. Long - A data type that's pretty much bigger than an int, in most cases, but is definitely smaller than a breadbox. Malloc() - A C library function used to slowly consume all system RAM. Sometimes not used on embedded systems to avoid memory leaks. Though malloc() does return an error code, most programmers know their code is perfect so never check it. Windows applications are immune from memory leaks since programmers can count on regular crashes to automatically release previously-allocated RAM. McCabe Cyclomatic Complexity - The scoring algorithm in the Great Game of Programming. The current high score is held by Eric Allman for Sendmail, though legions of developers are working hard to beat even that impressive record. Microsoft Project - A widely-used application that creates exquisitely-detailed colorful PERT and GANTT charts that no one reads or believes. MISRA C - A set of guidelines meant to stifle the artistic freedom of fun-loving C developers worldwide. Multicore processor - Moore's Law taken to the limit. A device that no one knows how to use and for which no tools exist. OOP - Acronym for Outrageously Obfuscated Programming. See Procedural Programming. Procedural Programming - The opposite of OOP, procedural programming is the art of exposing ones data to the entire system to facilitate easy interaction between components. Commonly used on systems bid on a cost-plus basis. Recursion - See Recursion. Reestimation - The process that follows the boss's shriek of rage when presented with a project's schedule. Also widely-used by the first wave of consultants hired to save a doomed project. Schedule - See Lie, Mendacity, Deceit, Distortion, Fantasy, Fraud, and Deception. Security - The art of ^H^H%6*((((buffer overflow PRIZE AWARD!!! THE INTERNATIONAL AWARENESS PROMOTION DEPARTMENT WISHES TO CONGRITULAET YOUR EXCELLCENIE'S LUCK IN WINNING $1,200,000 (ONE MILLON TWO HUNDERD THOUSAND). PLEASE FORWARD YOU COMPLEAT DETAILS URGENTLY. Soft core - See Firmware. Soft Real-time - An event that doesn't really have to be done within a certain timeframe, but that requires service, well, pretty fast. In a timely manner. Uh, like, don't make the user wait too long. So Linux, may it's name be forever blessed, is soft real-time, but Windows isn't. Got it? Syntax error - The absurd behavior of a compiler when it encounters the almost legitimate C code that worked fine on Manx C version 0.9 in the early 80s. SystemC - A technology that gives hardware developers all of the evils of software engineering. UML - Acronym for Unified Modeling Language, a technique for making pretty pictures no one understands. Warning - A message emitted by a compiler to try and convince the programmer that some program construct is likely confusing, wrong or dangerous. Because of the serious nature of warnings most compilers have a provision to turn them off. Watchdog Timer - the hardware and software used to reboot crashed code. Not used by developers who believe their code is perfect (see Delusional). Windows - The golden child of operating systems. Answer to life, the universe, and everything. Most excellent example of perfection. Utterly without fault. Maintained by a band of devoted faithful whose primary mission is to strike down all favorable references to *that* other operating system which was spawned by the devil, promoted by his evil minions, and used only by clueless Slashdot-reading newbies. Under no circumstances see Linux. Y2K - The first end of the world. Stay tuned for the Unix version in 2038. 8051 - The universal microcontroller architecture which was obsolete minutes after being introduced. In the year 10,000 AD someone, somewhere, will be writing 8051 code. Probably in COBOL. |
||||
| Failure of the Week | ||||
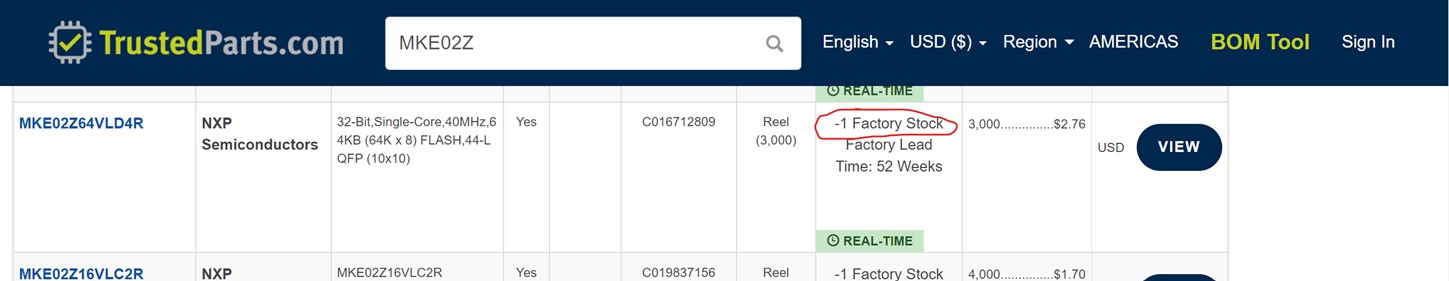
It seems TrustedParts feel that Joe Back owes them a CPU: Mark Peterson sent this: Have you submitted a Failure of the Week? I'm getting a ton of these and yours was added to the queue. |
||||
| This Week's Cool Product | ||||
Working on low-power projects? There are a number of tools to help measure the current and power used by these systems. A new one with an attractive price point ($249) is the MetaShunt. It is a high dynamic range current measurement device, capable of measuring from 10s of nanoamps up to 500mA. A control loop running at 490kHz ensures the burden voltage remains <40mV, and data is passed to your computer at 3.9kHz continuously or bursting up to 25.5kHz. More information can be found on the Hackaday page here. It is for sale on Tindie. Hackster.io recently wrote a short article on it as well. Note: This section is about something I personally find cool, interesting or important and want to pass along to readers. It is not influenced by vendors. |
||||
| Jobs! | ||||
|
Let me know if you’re hiring embedded engineers. No recruiters please, and I reserve the right to edit ads to fit the format and intent of this newsletter. Please keep it to 100 words. There is no charge for a job ad.
|
||||
| Joke For The Week | ||||
These jokes are archived here.
|
||||
| About The Embedded Muse | ||||
|
The Embedded Muse is Jack Ganssle's newsletter. Send complaints, comments, and contributions to me at jack@ganssle.com. The Embedded Muse is supported by The Ganssle Group, whose mission is to help embedded folks get better products to market faster. |